


Next: 2.7 Inversion
Up: 2. Background: Encryption and
Previous: 2.5 Encryption Key
To produce understandable decrypted text, you need to decrypt the encrypted
text. Sometimes we might say decode or decipher instead of decrypt. To decrypt,
we undo encryption, i.e. ``run encryption in reverse'' to transform ciphertext
into plaintext, as shown Figure 4.
Figure 4:
Intermediate Decryption Example Using the Caesar Cipher
 |
Observe that Figure 4 has flipped the arrows
upside down to show that decryption transforms the bottom line into
the top line. Now, compare the character mappings used in
Figures 2 and 4:
- Figure 2: 'w'
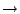 'z', 'e'
'z', 'e'
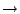 'h', the space maps to a space, 'a'
'h', the space maps to a space, 'a'
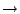 'd', 'p'
'd', 'p'
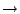 's', and so forth.
's', and so forth.
- Figure 4: 'w'
 'z', 'e'
'z', 'e'
 'h', the space maps to a space, 'a'
'h', the space maps to a space, 'a'
 'd', 'p'
'd', 'p'
 's', and so forth.
's', and so forth.
The mappings in Figure 4 reverse the mappings in
Figure 2, which corresponds to the idea of ``running
encryption in reverse''. So, to form the decryption key for decoding
ciphertext, reverse all the mappings in the encryption key.
Figure 5 shows this process for the encryption
key from Figure 1.
Figure 5:
Intermediate Decryption Key for the Caesar Cipher
 |
For conciseness and consistency omit arrows but understand that they
implicitly point down. So, you must flip
Figures 4
and 5 upside down, yielding
Figures 6 and 7. Figure 8
summarizes the different types and arrangements of keys.
Figure 6:
Final Decryption Example Using the Caesar Cipher
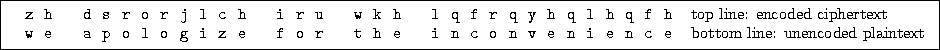 |
Figure 7:
Final Decryption Key for the Caesar Cipher
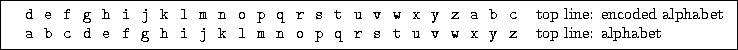 |
Figure 8:
Summary of Keys
 |



Next: 2.7 Inversion
Up: 2. Background: Encryption and
Previous: 2.5 Encryption Key
Thomas Yan
2000-05-01
